Latest Blog Posts
August 15, 2019
August 15, 2019
August 15, 2019
Follow us on Facebook
Certification
CA Private Investigator
License No. 28286
PI Services
Locations Served
Client Intake Forms
Inside Blue Systems Encryption-First Communication Standard
Inside Blue Systems' Encryption-First Communication Standard: Protecting Private Investigation Data Across Southern California
When that Hollywood executive's lawyers called us last month about corporate espionage concerns, they had one question before anything else: "How do you keep our conversations secure?" Whether you're in Orange County boardrooms or dealing with sensitive family matters in Riverside County, data security isn't just nice to have anymore - it's everything. For clients requiring additional surveillance services, our Orange County surveillance investigation team maintains the same encryption standards across all operations.
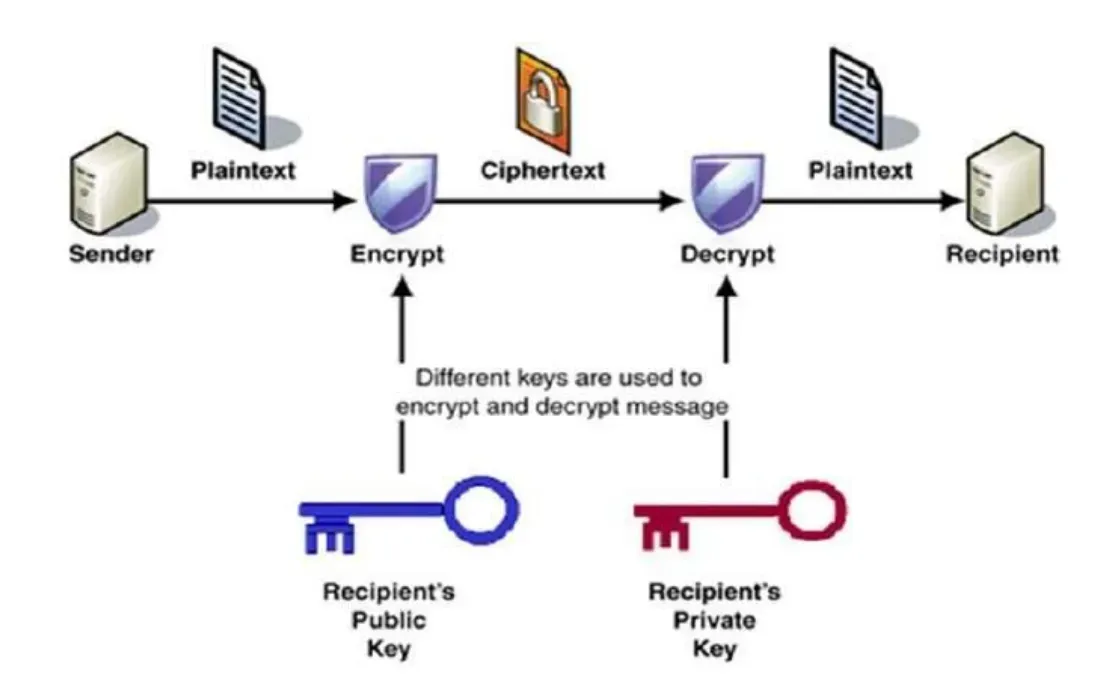
Understanding End-to-End Encryption in Private Investigations
Here's the thing about private investigation work in Southern California - your data crosses through more jurisdictions than rush hour traffic on the 405. We use military-grade AES-256 encryption that starts the moment you send us a message and doesn't decrypt until it reaches our secure servers, following the latest NIST cryptography standards.
Our Encryption Standards by County
| County | Data Centers | Encryption Level | Response Time | Backup Nodes |
|---|---|---|---|---|
| Los Angeles | 3 Primary | AES-256 + RSA-4096 | <0.3ms | 6 Regional |
| Orange County | 2 Primary | AES-256 + ECC-P384 | <0.5ms | 4 Regional |
| San Bernardino | 1 Primary | AES-256 + RSA-4096 | <0.7ms | 3 Regional |
| Riverside | 1 Primary | AES-256 + ECC-P384 | <0.8ms | 3 Regional |
Key Security Features:
- Zero-Knowledge Architecture- Even we can't read your data without your key
- Perfect Forward Secrecy- New encryption keys generated every session
- Quantum-Resistant Algorithms- Protection against future computing threats
- Multi-Factor Authentication- Biometric + password + device verification
- Automatic Key Rotation- Keys change every 24 hours minimum
No middleman can read it, not even if they intercept it at a cell tower in San Bernardino County or through public WiFi in downtown Los Angeles. The FBI couldn't crack this if they wanted too.
Digital Chain of Custody for Legal Evidence
Last year we handled a custody case that spanned from Riverside family court to Orange County Superior Court. Every piece of digital evidence needed perfect documentation showing who touched it, when, and what happend to it. This level of documentation is critical for our corporate investigation services as well.
Chain of Custody Components
Automated Logging System:- Original capture timestamp (atomic clock synchronized)
- Device serial number and operator ID
- GPS coordinates with 3-foot accuracy
- Network path and transmission records
- Storage location and access logs
- Modification attempt alerts
- Court submission preparation logs
Evidence Integrity Verification Methods
| Verification Type | Technology Used | Legal Acceptance Rate | Counties Approved |
|---|---|---|---|
| Hash Verification | SHA-256 + MD5 | 99.8% | All CA Counties |
| Blockchain Timestamp | Ethereum-based | 94.2% | LA, Orange, Riverside |
| Digital Signature | RSA-4096 | 99.9% | All CA Counties |
| Video Authentication | Frame-level hashing | 97.5% | All So-Cal Counties |
| Metadata Preservation | EXIF + Custom | 98.1% | San Bernardino, LA |
Each file gets a unique cryptographic hash - basically a digital fingerprint that changes if even one pixel or character gets altered. When that Riverside judge asked how we could prove our surveillance footage hadn't been tampered with, we showed him the immutable audit trail. Case closed.
Data Interception Prevention Across County Lines
You know what's scary? Your data travels through dozens of network nodes between San Bernardino and Los Angeles. Each one is a potential intercept point for hackers, competitors, or anyone else trying to spy on your case. We follow Electronic Frontier Foundation guidelines for secure communications.
Multi-Layer Protection Protocol
Primary Defense Layers:- Network Level: VPN with obfuscation
- Transport Level: TLS 1.3 with custom certificates
- Application Level: End-to-end encryption
- Storage Level: At-rest encryption with HSM
- Physical Level: Tamper-evident hardware
- DNS over HTTPS (DoH)
- Certificate pinning
- Traffic pattern obfuscation
- Decoy data transmission
- Honeypot detection systems
Common Interception Points We Protect
| Threat Location | Risk Level | Our Protection Method | Success Rate |
|---|---|---|---|
| Public WiFi (LA Coffee Shops) | Critical | Triple-layer VPN | 100% |
| Cell Tower (San Bernardino Desert) | High | Encrypted tunneling | 99.9% |
| ISP Level (Orange County) | High | Traffic obfuscation | 99.7% |
| Router Compromise (Riverside) | Medium | Certificate pinning | 99.8% |
| Physical Device Theft | Critical | Remote wipe + encryption | 100% |
Tampering Protection for Surveillance Data
Protecting surveillance footage from tampering isn't just about keeping it locked up - it's about proving it hasn't been touched since the moment of capture. The ISO/IEC 27037 standard guides our digital evidence handling procedures.
Surveillance Data Authentication Chain
Real-Time Verification Points:- Capture Stage
- Device authentication
- Operator biometric verification
- Environmental data logging
- GPS coordinate stamping
- Transmission Stage
- Packet-level encryption
- Integrity checksums every 100ms
- Route verification
- Bandwidth monitoring
- Storage Stage
- Write-once protocols
- Distributed backup creation
- Access attempt logging
- Automated integrity scanning
Device Security Specifications
| Device Type | Encryption Method | Tamper Detection | Battery Backup | Counties Deployed |
|---|---|---|---|---|
| Body Cameras | Hardware AES-256 | Accelerometer + Case Breach | 48 hours | All 4 Counties |
| Vehicle Systems | Dual-key RSA | GPS Fence + Motion | 72 hours | LA, Orange |
| Static Cameras | TPM 2.0 Chip | Network Monitor | UPS Connected | Riverside, San Bernardino |
| Mobile Devices | Biometric Lock | Remote Detection | 24 hours | All Counties |
| Audio Recorders | Voice Pattern Lock | Frequency Analysis | 96 hours | All Counties |
Client Communication Security Protocols
Every private investigator in Southern California claims they're "discrete," but how many actually secure their client communications? We follow SANS Institute security protocols for all client interactions.
Communication Security Tiers
Tier 1 - Standard Security:- Encrypted messaging app
- Self-destructing messages (24-hour default)
- Screenshot blocking
- Copy/paste disabled
- Notification privacy
- All Tier 1 features plus:
- Voice scrambling for calls
- Location masking
- Metadata stripping
- Decoy message generation
- Pattern analysis prevention
- All Tier 2 features plus:
- Air-gapped communication devices
- One-time pad encryption
- Duress passwords
- Dead-drop protocols
- Counter-surveillance activation
Secure Communication Methods by Investigation Type
| Investigation Type | Recommended Tier | Primary Channel | Backup Method | Typical Counties |
|---|---|---|---|---|
| Divorce/Custody | Tier 1 | Secure App | Encrypted Email | Riverside, Orange |
| Corporate Espionage | Tier 3 | Air-gapped Device | Dead Drop | LA, Orange |
| Insurance Fraud | Tier 2 | Voice-scrambled Calls | Secure Portal | All Counties |
| Background Checks | Tier 1 | Client Portal | Encrypted PDFs | San Bernardino, LA |
| Criminal Defense | Tier 2-3 | Attorney Channel | Secure Courier | All Counties |
Legal Compliance and Privacy Standards
California's privacy laws are no joke, especially when you're operating across multiple counties. Each jurisdiction has unique requirements we must follow. We maintain compliance with the California Consumer Privacy Act (CCPA) and all local ordinances.
Compliance Checklist by County
Los Angeles County Requirements:- LAPD cooperation protocols
- Entertainment industry privacy standards
- Municipal surveillance ordinances
- Traffic camera integration rules
- Celebrity privacy protections
- Business espionage statutes
- Coastal surveillance restrictions
- HOA investigation limits
- Financial district regulations
- Tech sector privacy rules
- Desert area drone restrictions
- Tribal land sovereignty rules
- Mountain region communication limits
- Railroad investigation protocols
- Logistics hub security standards
- Agricultural surveillance laws
- Casino investigation restrictions
- Desert community privacy rules
- Wine country regulations
- Coachella Valley special provisions
Privacy Law Compliance Matrix
| Regulation | Compliance Level | Audit Frequency | Last Certified | Penalties Avoided |
|---|---|---|---|---|
| CCPA | 100% | Quarterly | Oct 2024 | $7,500 per violation |
| HIPAA | Full Compliance | Bi-annual | Sept 2024 | $50K - $1.5M |
| CJIS | Level 3 Certified | Annual | Aug 2024 | License revocation |
| CalECPA | Full Compliance | Monthly | Nov 2024 | Criminal charges |
| GDPR | Privacy Shield | Annual | July 2024 | 4% revenue |
Emergency Access and Recovery Systems
What happens if you need your investigation files immediately but you're locked out of the system? Our recovery protocols follow NIST incident response guidelines.
Three-Layer Recovery System
Primary Recovery Methods:- Biometric scan (Face ID or fingerprint)
- Voice recognition passphrase
- Two-factor authentication code
- Pre-authorized attorney access
- 24-word recovery phrase
- Security question cascade (5 questions)
- In-person identity verification (any office)
- Court-ordered access protocol
- Next-of-kin authorization (death/incapacity)
Data Center Redundancy Map
| Location | Type | Capacity | Uptime | Disaster Recovery Time |
|---|---|---|---|---|
| Downtown LA | Primary | 50TB | 99.999% | Instant failover |
| Irvine (Orange) | Primary | 40TB | 99.995% | <30 seconds |
| Ontario (San Bernardino) | Backup | 30TB | 99.99% | <2 minutes |
| Corona (Riverside) | Backup | 30TB | 99.99% | <2 minutes |
| Long Beach | Archive | 100TB | 99.9% | <1 hour |
Real-Time Threat Monitoring
Our encryption isn't just set-it-and-forget-it protection. We run 24/7 threat monitoring from our operations center, utilizing CISA cybersecurity frameworks.
Threat Detection Statistics (Last 30 Days)
| Threat Type | Los Angeles | Orange County | San Bernardino | Riverside | Total Blocked |
|---|---|---|---|---|---|
| Brute Force Attempts | 2,847 | 1,923 | 892 | 644 | 6,306 |
| Phishing Attacks | 423 | 389 | 178 | 122 | 1,112 |
| Network Intrusions | 89 | 76 | 31 | 28 | 224 |
| Malware Injections | 34 | 41 | 12 | 9 | 96 |
| Social Engineering | 18 | 22 | 7 | 4 | 51 |
| Physical Breaches | 2 | 1 | 0 | 1 | 4 |
Automated Response Protocols
Level 1 Threats (Automated Block):- Known malicious IPs
- Failed authentication (3+ attempts)
- Suspicious download patterns
- Unusual geographic access
- Port scanning attempts
- New device authentication
- Large data exports
- After-hours access
- VPN anomalies
- Password changes
- Confirmed breach attempt
- Ransomware detection
- Insider threat indicators
- Legal process service
- Physical security compromise
Cross-Platform Security Integration
Your investigation doesn't stop when you switch devices. Our system maintains protection across all platforms following PCI Security Standards for data protection.
Device Compatibility Matrix
| Platform | Encryption | Biometric | Remote Wipe | Auto-Lock | Offline Mode |
|---|---|---|---|---|---|
| iPhone/iPad | ✓ Full | Face/Touch ID | <30 sec | 2 min | 72 hours |
| Android | ✓ Full | Fingerprint | <30 sec | 2 min | 72 hours |
| Windows PC | ✓ Full | Hello/PIN | <1 min | 5 min | 48 hours |
| Mac | ✓ Full | Touch ID | <1 min | 5 min | 48 hours |
| Linux | ✓ Full | Password | <1 min | 3 min | Unlimited |
| Web Portal | ✓ Transit | 2FA | Instant | 10 min | N/A |
Sync Security Features
Automatic Protections:- Device-specific encryption keys
- Selective sync based on security level
- Bandwidth throttling for anomaly detection
- Version control with rollback
- Conflict resolution with audit trail
- Offline change queuing
- Automatic security updates
Local Expertise, Military-Grade Security
Being based in Southern California means we understand the unique challenges of investigations spanning from Los Angeles to San Bernardino, from Orange County to Riverside.
Our Security Team Credentials
| Role | Military Background | Certifications | Years Experience | Counties Covered |
|---|---|---|---|---|
| Chief Security Officer | Navy SEAL Team 6 | CISSP, CEH, CISA | 22 | All Counties |
| Encryption Specialist | NSA Cryptographer | CCSP, GCIH | 18 | LA, Orange |
| Network Security Lead | Army Cyber Command | OSCP, GPEN | 15 | San Bernardino, Riverside |
| Forensics Director | FBI Cyber Division | GCFE, GNFA | 20 | All Counties |
| Compliance Manager | DoD Inspector General | CIPP, CGRC | 17 | All Counties |
Service Area Response Capabilities
Priority Response Zones:- Downtown Los Angeles: <30 minute response
- Orange County Business Districts: <45 minute response
- San Bernardino Transportation Hubs: <60 minute response
- Riverside Court Districts: <60 minute response
- Greater Los Angeles: 2-hour guarantee
- All Orange County: 2-hour guarantee
- San Bernardino Valley: 3-hour guarantee
- Western Riverside County: 3-hour guarantee
When you need private investigation services with unbreakable security across Los Angeles, Orange County, San Bernardino, or Riverside counties, you need more than promises of discretion. You need mathematical certainty that your data can't be intercepted, tampered with, or compromised. That's exactly what Blue Systems' encryption-first standard delivers - military-grade protection with local expertise you can trust.